A narrative is a story or an account of events, experiences, or a series of related occurrences that are presented in a particular sequence to create meaning or convey a message. In the context of your organization, a narrative can be thought of as the way in which your organization tells its story to its audience, including customers, employees, investors, and other stakeholders.
Lights, Cameras...Practice! Investing in Media Training
Critical to your organization’s strategy to sell products & services, protect organizational reputation, and recover from crises is investing the time to engage traditional media. Unfortunately, many organizations fail to consider the importance that the media maintains in ensuring they achieve their goals and objectives, especially during time of crises.
Deepfake...a New Online Trend of Misinformation
Deepfake: Where Personal and Cyber Security Intersect? Part 1
In Part 1, Soteryx examines the technology of deepfakes—phony video, audio that looks…real. In Part 2 we will examine legal and political ramifications, though one can guess those easily should a digital video which looks authentic impugns a product or firm’s business reputation or purports to release personal, private information about a customer or client…or a foreign power or rival political party shows an elected official sleeping through critical policy meetings. Indeed deepfake engages the dead, where technology has been used not only to resurrect dead actors in TV/film fiction, but also in factual presentations, where deceased celebrity chef Anthony Bourdain’s voice was manufactured for a recent documentary, or avant-garde artist Salvador Dali engages visitors to the museum dedicated to him in St. Petersburg, Florida.
The Tech of “Real” Fakery and Misinformation
Over the past ten years, the tech industry has put a focus on developing increasingly competent artificial intelligence (A.I.) technologies in order to expedite processes that would have previously required human involvement or wouldn’t have been possible altogether. The results have been impressive, as A.I. algorithms have made their way into everything from website search engines to virtual assistant devices (e.g. Google Home or Amazon Echo smart speakers). By learning from the wealth of information present on the internet, as well as user inputs, A.I. technologies are consistently becoming smarter and more lifelike. However, this type of technology’s ability to learn from the information that it is fed is increasingly being used for malicious purposes–especially the spread of misinformation on social media platforms.
Here is a scary example featuring Facebook Chair Mark Zuckerberg supposedly confessing to the platform’s nefarious aims, greed.
No recent A.I. technology has posed as great of a threat to legitimate news and information online as deepfakes. This kind of A.I. functions by processing video and audio data of one or more people in order to learn their appearances and mannerisms which it then uses to create a highly realistic fake video of the main targeted person. In the case of celebrities or politicians, who usually tend to have a wealth of video and audio recordings publicly available online, deepfake programs have much more data to work with and can thus create increasingly convincing media featuring these targets. Though the concept of swapping the faces and voices of public figures to create a fake piece of media is not new, the neural A.I. networks that allow deepfakes to function are, and their ability to effortlessly learn from existing data is both powerful and problematic.
According to Mika Westerlund, the technology behind deepfakes can carry benefits for film, advertisement, and other industries. For example, this technology has helped film companies add the face of an existing actor onto that of another even after that actor’s death. However, the greater threat deepfakes pose to society cannot be ignored. For one, Westerlund explains that the proliferation of misinformative deepfakes can threaten individuals through their ability to be utilized as blackmail. More generally, the misinformative capability of deep fakes poses an especially important threat to the legitimacy of news sources and governments. Konstain A. Pantserev adds that deepfake technology is directly following in the footsteps of fake news as a veritable psychological weapon that can equally be used to sway the beliefs of certain online communities. Additionally, access to deepfake creation programs such as FakeApp signifies that the creation and further proliferation of these kinds of videos is only becoming easier for the average online user.
Though deepfakes will likely play an important role in contributing to new online trends of misinformation, solutions are being developed to combat the proliferation of these videos. In the case of deepfakes created as personal blackmail (a trend that began in 2017), many social media websites have banned posting such content altogether. However, identifying deepfakes in order to ban them appears to be the next challenge in the fight against the risks of this technology. In their study on the subject of exposing deepfakes, Li and Lyu propose a solution that involves using their own A.I. program to detect if a video is a deepfake by analyzing if it contains visual traces–or “warping artifacts''– that are often attributed to the imperfections of the A.I. algorithms that produce deepfakes. Many researchers propose following such a model, as current deepfake-producing programs produce visual artifacts that countering A.I. programs can easily identify. However, new methods will need to be developed as this type of A.I. improves.
How can I protect yourself, my family, my business?
Contact us at https://www.soteryx.com/contact and we will break down how we can help secure you, your reputation, your business’s physical and cyber infrastructure, adding both value and peace of mind.
*Christopher Chambers is EVP and General Counsel at Soteryx Corp. Tristan Schentzler is a senior at The University of British Columbia-Vancouver, majoring in International Relations and Journalism.
What’s Still Left to Do Regarding Internet of Things (IoT) Cybersecurity?
Digital Equity for All
The digital divide—the gap between students with sufficient knowledge of and access to digital technology and those without—for decades has been among the greatest challenges facing our education system. Digital technology equity, or the lack thereof, has negatively impacted minority students, low-income families, and rural student populations in disproportionate numbers.
Three Cybersecurity Mistakes Small Businesses Need to Stop...NOW!
You might be thinking that if Microsoft can get hacked why bother trying to protect your small business? Cyber security is too expensive. You would be wrong. Hacking, phishing, ransomware, etc. are threats to every business – big or small. Worse, the consequences are endless, lawsuits, loss of revenue, loss of customers, diminished customer loyalty & trust, and more.
The Diversity Dividend: A Corporate Strategy to Build Brand Equity/Loyalty Across Communities
A report by global management consulting firm McKinsey & Company, observing more than 300 companies in the US, Canada, the United Kingdom and Latin America, found that companies ranking in the top 25th percentile for gender diversity on their executive teams were 21 percent more likely to turn a profit above the national average.
Celebrating Women's History Month
Diversity and Inclusion efforts in the last few years is a recent endeavor that formally honors and supports their efforts by making the inclusion of women a concerted effort by all parties across industries. Soteryx celebrates the progress women have made this month by highlighting their stories of overcoming adversity through sheer determination and belief in self.
Pandemic Response: Emergency Risk Management Reference Matrix for Public Agencies, Private Business, Schools & Healthcare Providers
Soteryx’s purpose is to provide clients and potential customers with a matrix for best practices and sound risk management preparedness regarding pandemics and other mass illness occurrences with the potential to disrupt commerce and everyday life. This is in outline form for ease of reference, accordingly.
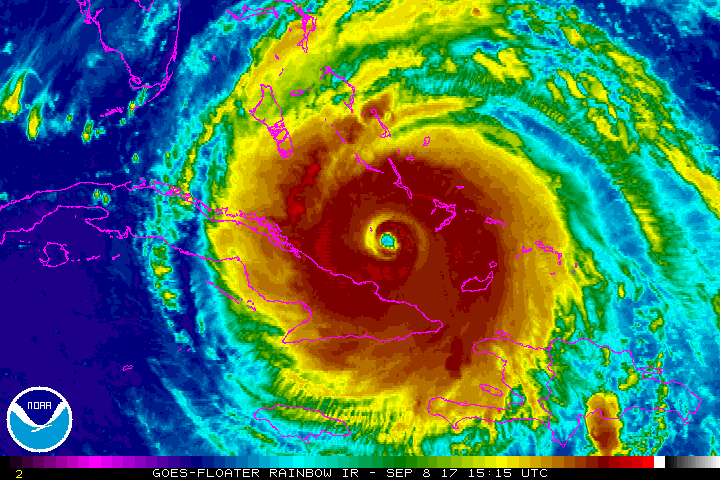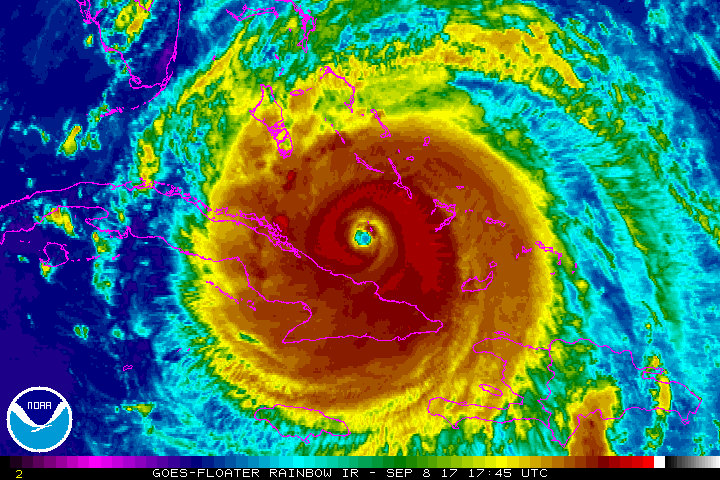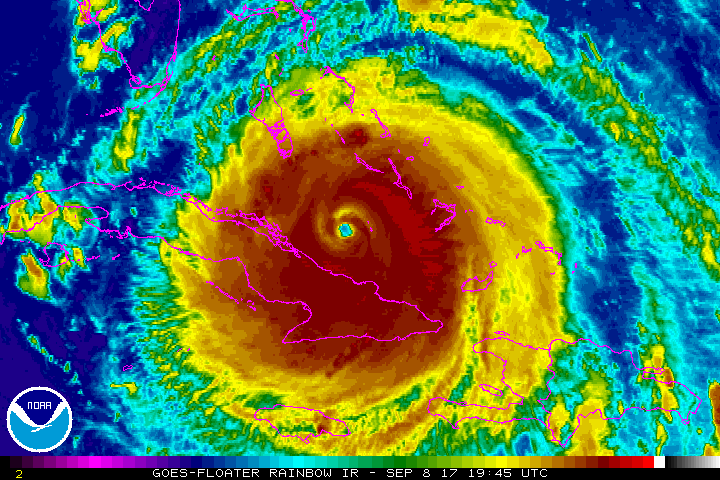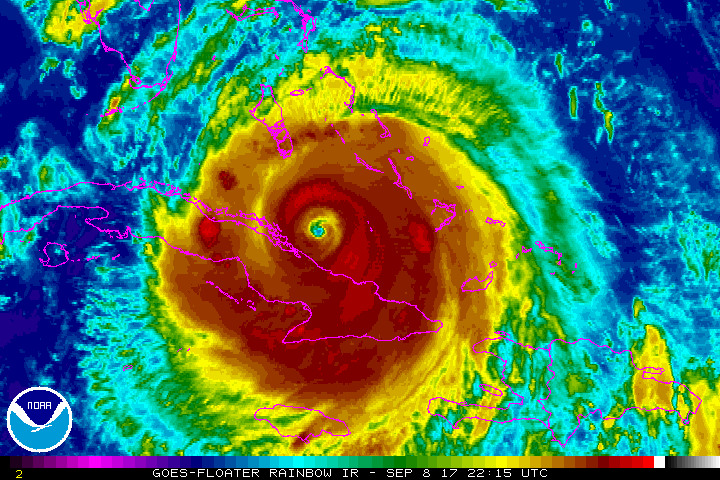
Hurricane on the Horizon...Some Tips to Get You Properly Prepared
Attacks on Your Data…and How the Cloud can get You out of the Rain
It can be daunting without customer-oriented IT or security consultants to break down components and how they fit the new universe of data and storage. You’ve heard of the “cloud,” you likely have it for you phone and even your home computer, you know it’s the current go-to solution for businesses rather than hard storage and bulky servers in your office coat closet.
Active Shooter Realities: How to Prepare for the Unthinkable
The FBI defines an active shooter as one or more individuals actively engaged in killing or attempting to kill people in a populated area. Tragically, in 2018 the U.S. experienced 27 active shooter events across 16 states. With the 27 events, the FBI recorded a total of 85 people killed with 128 people wounded.
Looking out a bit further from 2000 through 2017, FBI statistics show us that the U.S. experienced a total of 250 active shooter incidents that left 799 people dead and 1,418 casualties. The statistics point to 2017 as the most violent year for active shooters, yielding 138 deaths and 591 casualties.
The 2000 through 2017 statistics show us that businesses experienced the most active shooter events with more than one third (38%) of the occurrences happening at the workplace. Schools followed businesses with a recorded total of 14.8% incidents.
The FBI statistics tell us that an active shooter incident can occur anywhere. As the U.S. mourns the recent tragic active shooter events it is important to keep front of mind what you need to do to help protect yourself during an active shooter event.
Here are some tips:
First, and foremost, get away if you can. Stay low and run away from the shooter or the sound of the gunshots. Do not run in a straight line. Make your movement unpredictable such as running in a zig zag motion.
If you cannot get away, find cover. Cover is anything that can effectively shield you from gunfire. Remember, most active shooters use high-powered rifles, assault weapons or semiautomatic guns, so the bullets will have a higher penetrating power. Do your best to find cover that also conceals you. Stay behind cover until you can get away, or until the police secure the scene.
If you cannot get away or find cover, then find concealment. In other words, hide so the shooter can’t see you. Be acutely aware that concealment is not cover and cannot protect you from gunfire.
Always remember, law enforcement is on the way. In most cases, the police respond quickly to an active shooter incident; therefore, you are trying to buy yourself time.
During any of these courses of action, if you encounter the police, it is imperative that you make sure to let them know that you’re not a threat. Police have a saying, “It’s the hands that will hurt you.” Raise your arms, open your hands, and obey their commands. They’re there to help you.
In the end, just know that in order to increase your chances for survival, you have to take action. Do something! Don’t let fear paralyze you.
A Cybersecurity Primer for Healthcare Practices
10 Actions That Your Business Needs to Do to Help Avoid a Cyber Breach
As the Equifax, Target, Marriott, and Yahoo breaches have made clear, businesses worldwide need to prepare for cyber breaches or face the possibility of catastrophic loss in time, money, and reputation. To ready your business for the ever looming threat of a cyber breaches, here are 10 simple precautions you need to implement ASAP.
5 Tips for Marketing Your Company on Social Media
6 Steps for Protecting Your Social Media Accounts from Being Hacked
2018 research revealed approximately 22% of social media users confirmed that their online accounts have been breached by hackers at least once, and 14% of social media users confirmed that their accounts have been breached more than once. You really don’t want that heart-sinking sinking feeling that happens when you learn that your social media account has inflammatory, vile, and/or just mean posts that you did not write. Here are 6 steps for protecting your social media accounts.